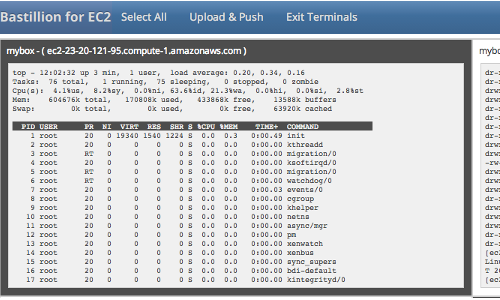
A modern, web-based SSH console and key management tool for Amazon EC2.
Bastillion for EC2 provides a browser-based SSH management platform designed specifically for AWS environments.
It enables secure access, auditing, and centralized key management across all your EC2 instances—built on the same foundation as Bastillion and now updated for Java 21 / Jakarta EE 11.
- Upgraded to Java 21 and Jakarta EE 11
- Full support for Ed25519 (default) and Ed448 SSH keys
- New daemon mode for Jetty startup (
--daemon) - Updated dependencies for improved security and performance
- Clarified AWS IAM and EC2 integration steps
Free: https://github.com/bastillion-io/Bastillion-EC2/releases
AWS Marketplace: https://aws.amazon.com/marketplace/pp/prodview-e2pbdearyxwuk
apt-get install openjdk-21-jdkOracle JDK download: http://www.oracle.com/technetwork/java/javase/downloads/index.html
| Application | Android | iOS |
|---|---|---|
| Authy | Google Play | iTunes |
| Google Authenticator | Google Play | iTunes |
Download: https://github.com/bastillion-io/Bastillion-EC2/releases
Linux / macOS
export JAVA_HOME=/path/to/jdk
export PATH=$JAVA_HOME/bin:$PATHWindows
set JAVA_HOME=C:\path\to\jdk
set PATH=%JAVA_HOME%\bin;%PATH%Foreground (interactive):
./startBastillion-EC2.shDaemon (background):
./startBastillion-EC2.sh --daemonLogs are stored in jetty/logs/YYYY_MM_DD.jetty.log.
Enable debug output:
./startBastillion-EC2.sh -dStop:
./stopBastillion-EC2.shAccess in browser:
https://<server-ip>:8443 (or for AMI instances: https://<instance-ip>:443)
Default credentials:
username: admin
password: changeme
(For AMI, the password defaults to the EC2 Instance ID.)
- Configure an IAM Role with your Account ID and set the generated ARN in Bastillion-EC2.
- Import the Bastillion-EC2 public SSH key into the AWS EC2 console.
- Launch EC2 instances using that key pair.
- Start composite SSH sessions or run scripts across multiple instances.
- Add instance administrator accounts as needed.
More info: https://www.bastillion.io/docs/bastillion-ec2/index.html
Administrative access can be restricted through tags defined in a user’s profile.
Profile tags must match the EC2 instance tags set in AWS.
Examples:
tag-name
tag-name=mytag
tag1=value1,tag2=value2
Specify a custom SSH key pair or let Bastillion E2 generate its own on startup:
# Regenerate and import SSH keys
resetApplicationSSHKey=true
# SSH key type ('rsa', 'ecdsa', 'ed25519', or 'ed448')
# Supported options:
# rsa - Classic, widely compatible (configurable length, default 4096)
# ecdsa - Faster, smaller keys (P-256/384/521 curves)
# ed25519 - Default and recommended (≈ RSA-4096, secure and fast)
# ed448 - Extra-strong (≈ RSA-8192, slower and less supported)
sshKeyType=ed25519
# Private key
privateKey=/Users/you/.ssh/id_rsa
# Public key
publicKey=/Users/you/.ssh/id_rsa.pub
# Passphrase (leave blank if none)
defaultSSHPassphrase=myPa$$w0rdOnce registered, you can remove the key files and passphrase from the configuration.
Enable in Bastillion-EC2Config.properties:
jaasModule=ldap-olConfigure jaas.conf:
ldap-ol {
com.sun.security.auth.module.LdapLoginModule SUFFICIENT
userProvider="ldap://hostname:389/ou=example,dc=bastillion,dc=com"
userFilter="(&(uid={USERNAME})(objectClass=inetOrgPerson))"
authzIdentity="{cn}"
useSSL=false
debug=false;
};
Map LDAP roles to Bastillion profiles:
ldap-ol-with-roles {
org.eclipse.jetty.jaas.spi.LdapLoginModule required
debug="false"
useLdaps="false"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
hostname="<SERVER>"
port="389"
bindDn="<BIND-DN>"
bindPassword="<BIND-DN PASSWORD>"
authenticationMethod="simple"
forceBindingLogin="true"
userBaseDn="ou=users,dc=bastillion,dc=com"
userRdnAttribute="uid"
userIdAttribute="uid"
userPasswordAttribute="userPassword"
userObjectClass="inetOrgPerson"
roleBaseDn="ou=groups,dc=bastillion,dc=com"
roleNameAttribute="cn"
roleMemberAttribute="member"
roleObjectClass="groupOfNames";
};
Users are added/removed as they authenticate when their role matches a Bastillion profile.
Auditing is disabled by default.
Enable in log4j2.xml by uncommenting:
io.bastillion.manage.util.SystemAuditaudit-appender
https://github.com/bastillion-io/Bastillion-EC2/blob/master/src/main/resources/log4j2.xml#L19-L22
Then set in Bastillion-EC2Config.properties:
enableInternalAudit=trueSpecial thanks to these projects that make Bastillion possible:
Third-party dependencies are listed in 3rdPartyLicenses.md
Bastillion-EC2 is distributed under the Prosperity Public License.
Loophole, LLC — Sean Kavanagh
Email: [email protected]
Instagram: @spkavanagh6